
Cybersecurity Insights: IT Security Execs on Social Media
By Carter Hostelley
It’s rare that a day goes by without breaking news of some DDoS, ransomware, data breach, or other cyber-attack on a Fortune 1000 company. Clearly, doing business in the digital realm is neither safe nor secure. As a matter of fact, Cybersecurity Ventures predicts there will be $1 trillion spent globally on cybersecurity products and services over the next 5 years. Plus, the Bureau of Labor Statistics shows the rate of growth for jobs in information security is booming.
To stay up-to-date on the latest incidents and look for new ways keep cyber-criminals at bay, many IT security professionals are tapping into social media.
“Information security professionals are quite active on social media. They use it to find out about new vulnerabilities, comment on articles, and research security. They also use social media to network with other professionals and to get their ideas out there,” says Bryan Brake, co-host of the popular Brakeing Down Security podcast.
This means, for those interested in this burgeoning group of mission-critical security pros, social media can provide insights into the conversations they’re having, what they’re reading and sharing, and who’s influencing them on a daily basis.
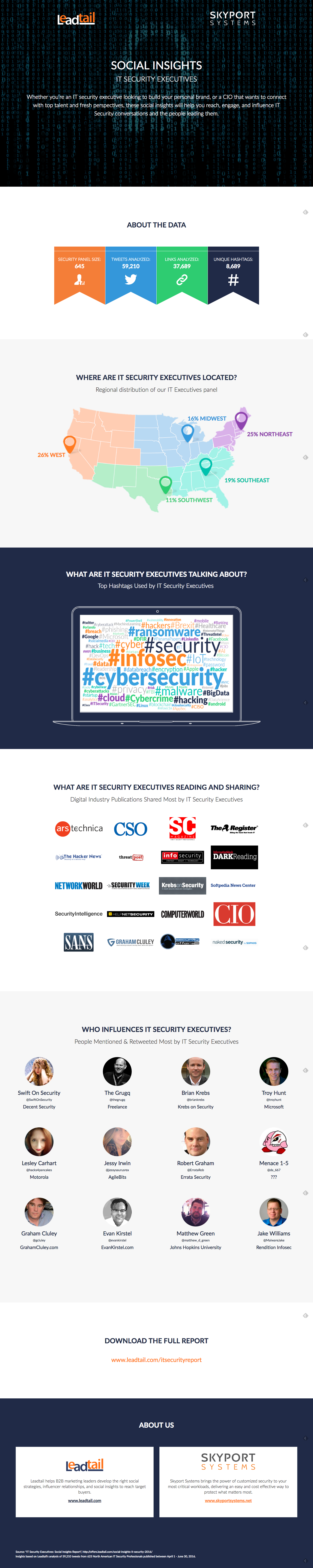
While social listening platforms typically analyze conversations that the general public is having around key terms, a report on IT Security Executives by Leadtail and Skyport Systems, specifically sheds light on how cybersecurity professionals are engaging on social media. The following discussion highlights some of the most relevant takeaways from this milestone report.
Who is leading the conversation on cybersecurity?
There are three main groupings of information security champions in the social media space; and each brings a different perspective on the problem set:
- Security Professionals: From chief information security officer (CISO) to the security engineer, these professionals ensure information assets and technologies are protected.
- CIOs: This is the C-Suite executive ultimately responsible for the (secured) technology operations of an enterprise organization
- Thought Leaders: This group includes journalists, bloggers, consultants, speakers, analysts, and investors with specific expertise in the different flavors of cybersecurity.
Who’s most influential with IT Security Pros?
Within these groupings, we’ve found there are certain people that cybersecurity professionals turn to again and again. And there are two telling characteristics that allow these influencers to break through the noise:
- They share a lot. These are not people who tweet out an article every couple of days. They are consistently sharing content that is interesting and insightful and appeals to the security audience.
- They are master curators that don't just blindly share articles and retweet others; they engage with personal comments and sometimes with extensive @reply threads.
In the world of cybersecurity the top influencers include:
- @briankrebs – Reporter and Publisher of KrebsonSecurity.com, Brian Krebs
- @hacks4pancakes – Security Incident Response Lead for Motorola Solutions, Lesley Carhart
- @gcluley – Computer security expert and blogger, Graham Cluley
- @MalwareJake – Founder Rendition InfoSec, Jake Williams
- @evanderburg – Director of Information Systems and Security at JURINNOV, Eric Vanderburg
- @weldpond – Co-Founder and CTO of Veracode, Chris Wysopal
- @jessysaurusrex – Vice President of Privacy and Security at Mercury, Jessy Irwin
Some Key Takeaways from the report
There were a number of key insights and takeaways from the report including:
1. The conversation is not only about cybersecurity
Our analysis of the top hashtags shared by this group shows that, yes, they talk a lot about #cybersecurity, #infosec, #security, #ransomware, #malware, and #hacking. But they’re also quite interested in conversations around #privacy, #bigdata, #cloud, and #IoT.
2. Different paths to influencing IT security professionals
There’s no single “right way” to become an influencer of IT security executives. Some influence by being expert curators, others through unique and original perspectives, while still others excel at engaging their audience through conversation and community.
3. C-Suite mindset but security perspectives
IT security executives read and share many of the same popular business publications as the rest of the C-suite, but they also turn to dedicated industry publications for insights and perspectives from other thought leaders and practitioners. These include: The Register, Dark Reading, Krebs on Security, Security Week, Help Net Security, and Security Affairs.
 __________________________________________________________________________________________________
__________________________________________________________________________________________________
Carter Hostelley is the Founder and CEO of Leadtail, a social strategy and insights firm. He’s a relentless advocate of the importance of social media to B2B CMOs and senior marketers; specifically, how social media can reach, engage, and influence buyers. He is also a contributing author at CMSWire, and has been quoted in numerous business publications including Forbes and The Wall Street Journal. The insights in this commentary come from Leadtail's "IT Security Executives" report in partnership with Skyport Systems. Download the full report here.
LinkedIn: www.linkedin.com/in/carterhostelley
Twitter: @carterhostelley
Website: www.Leadtail.com


